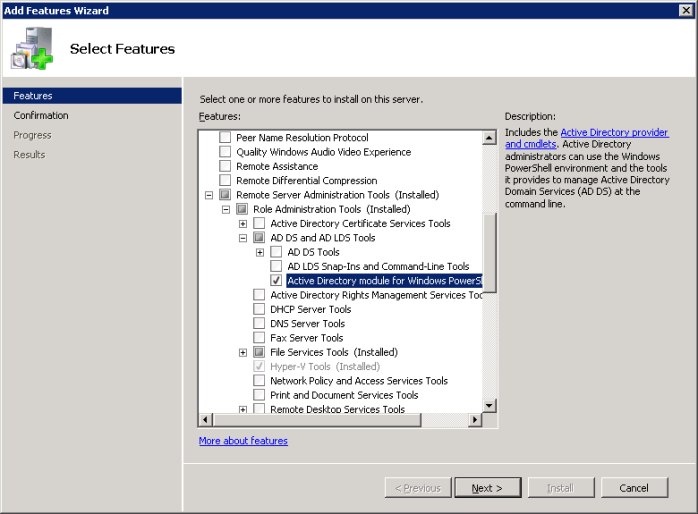
Install Domain Services using PowerShell
Open PowerShell and execute the below command
Install-WindowsFeature -name AD-Domain-Services
To install Active Directory Forest
install-ADDSForest -domainname “abc.com”
It will prompt you to enter the restore mode password and will do the same prerequisite check which perform by GUI installation also and it will install the domain controller. It will install the DNS and also Group Policy Management Console.
Install from Media
If you are in a large enterprise where thousands of domain controllers exists and the database size is hundred or thousand GB, install from media (IFM) method is the best choice. It will reduce the replication traffic that is initiated during the installation of an additional domain controller in an Active Directory domain. Reducing the replication traffic reduces the time that is necessary to install the additional domain controller.
Later on after installing from media (that could be an external drive, pen drive or DVD), the DC will only synchronizes the difference.
The Ntdsutil is a command-line tool that provides management facilities for Active Directory Domain Services (AD DS). You can use this tool to create installation media for a domain controller. Installation from media does not work across different operating system versions. In other words, you must use a Windows Server 2008 domain controller to generate installation media to use for another Windows Server 2008 domain controller installation.
Type of installation media parameter:
- Create Full
- Create RODC
- Create Sysvol Full
- Create Sysvol RODC
Sample command
create sysvol full

It will store the necessary files and folders as below

To promote a Server as AD from media, from the Server Manager select the Server and click on Promote this server to a domain controller.
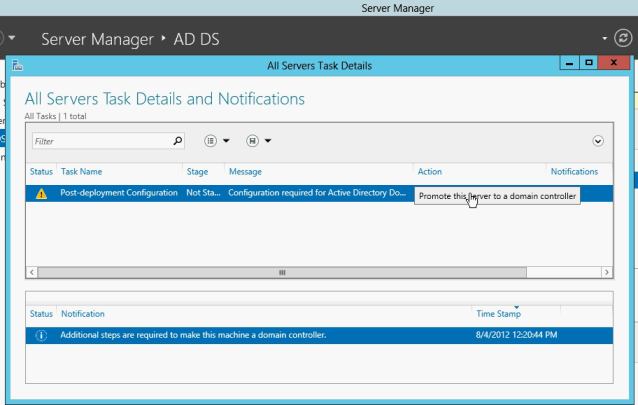
Select Add a Domain Controller to an existing domain option and click next
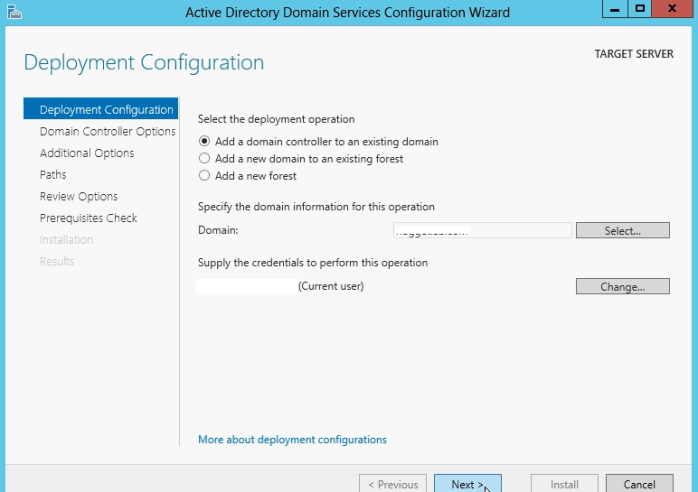
Select The domain controller options and click next

Click next in DNS options

In the Additional Options window check Install from media and select the appropriate path of media and click next

The wizard will now install the domain controller using installation media without connecting to network.
Demote a Domain Controller
To demote a domain controller, from the Server Manager go to Removes roles and features and click next in the wizard
Uncheck Active Directory Domain Services from roles

Click on Remove Features button

Click on Demote this domain controller link

Specify the Credential to execute the command and click next

Check Proceed to removal and click next
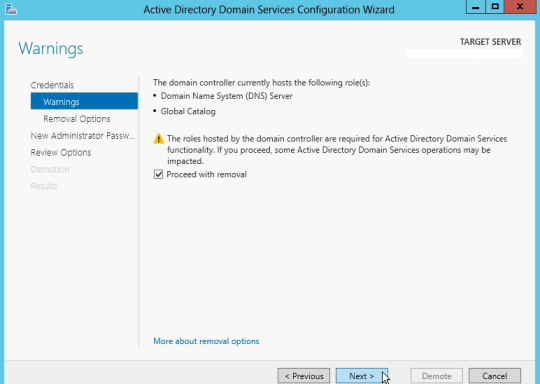
Check Remove DNS delegation and click next

Enter the new administrator password for your local computer account and click next

Click on Demote button

You can also demote a DC using PowerShell
Open command prompt
- Enter PowerShell
- Enter uninstall-addsdomaincontroller
- Enter local administrator password and Press Y to demote this server.
The domain controller which was decommissioned it has to be removed manually from Active Directory Sites and Services. To do this go to Active directory sites and services from Server Manager. Expand your site and right click on that DC which was demoted earlier and click Delete.

Planning an Active Directory Upgrade
Though there is no change in the function level but it is still required to upgrade to the newest forest functional level to upgrade from W2K8 to 2012. Run the below command:
adprep /forestprep
You need to do this only one domain controller in your forest. Because, it will replicate all the changes to all other domain controllers in your network automatically. To execute the forestprep command you need to have installation media and you should be the enterprise Administrator to run this command.
For domain functional level you need to have at least windows server 2003 function level or greater.
To check domain functional level go to Active Directory Users and Computes and Right Click on your domain name and click on Raise domain functional level menu. It will show you the current functional level of your domain.


Upgrade
As I have mentioned in my earlier article, there is no way to upgrade from full GUI to core. You have to use the same mode.
The Global Catalog Service
Before updating you should have some idea about the Global Catalog Services (GC).
- It is the full copy of host domain objects.
- There should be at least one GC in a single domain.
- It will do a partial read-only of other domain in the same forest.
- It gives you simpler searches across domains.
- It validates forest objects. For example in case of Universal group membership information, which can contain objects from different domain, Global catalog can validate universal group membership.
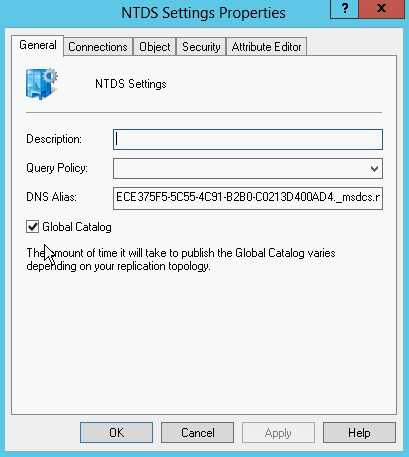
If you want to make a Domain Controller as a Global Catalog go to Active Directory Sites and Services
Expand the domain control and right click on NTDS settings. Check Global Catalog option to make it GC.
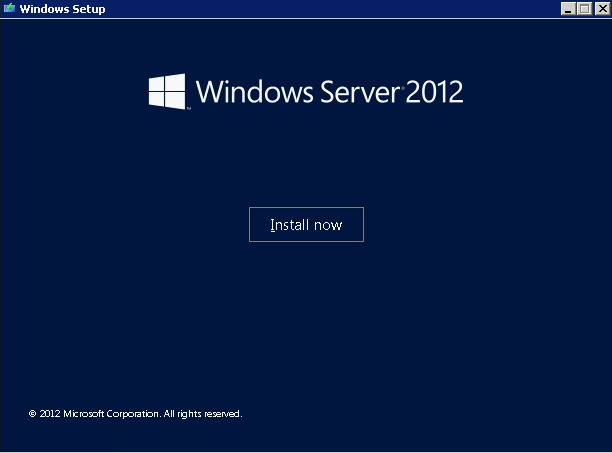
To upgrade a existing Domain Controller insert the Windows 2012 Server OS media and Click on Install Now
Ignore latest update check option. This function actually don’t install the drivers you needed on that server, it will only update whether any known drivers issue fixed by Microsoft.

Select the appropriate installation mode

Accept license agreement and click Next and Click on Upgrade

Ignore the warning and click next

The wizard will start upgrading you existing domain controller (win 2003/2008) to Windows 2012.
DNS SRV Records restore
The DNS SRV (Service Record) entries are critical for proper function of AD. It is a specification of data in the Domain Name System defining the location, i.e. the hostname and port number, of servers for specified services. This records are so important that if you delete any record accidently you domain service will not work properly.
So what can be done if any record deleted accidently?


Please note that, the netdiag /fix will not work anymore in Windows Server 2012 which use to work in the previous versions.
You can use below command which is very handy to restore all SRV records.
nltest /dsregdns
What more things new in AD (I have mentioned few of them in my earlier article also)
- DCPromo is deprecated, now it is built into UI. ADPrep other prerequisites are now very well handled
- Active Directory Administrative center has improved UI and have PowerShell history

- By default Powershell execution is restricted. You can enable it by using Set-ExecutionPolicy cmdlet (http://technet.microsoft.com/en-us/library/ee176961.aspx) Set-ExecutionPolicy Unrestricted
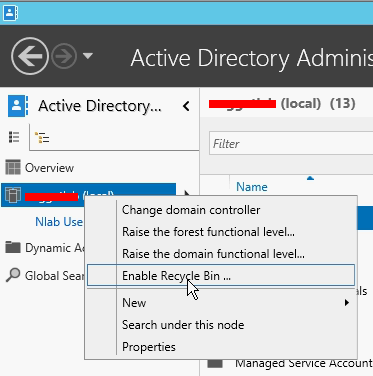
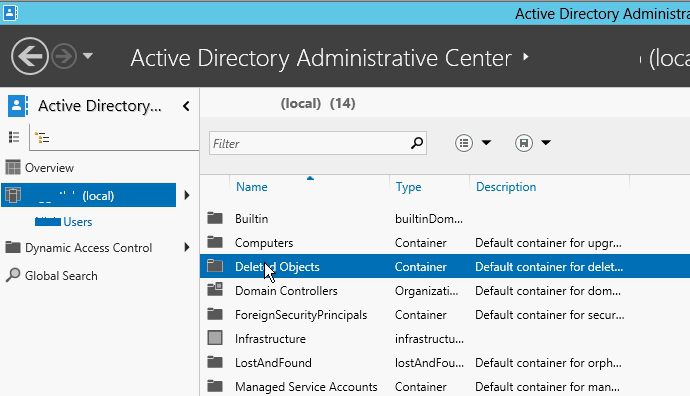
- Active Directory Recycle bin – will allow you to recover the objects you accidentally deleted. You need to enable that functionality first. For example, to enable Active Directory Recycle Bin for contoso.com, go to Server Manager and Click on Active Directory Module for Windows PowerShell form Tools menu and type the following command, and then press ENTER:

- Enable-ADOptionalFeature –Identity ‘CN=Recycle Bin Feature,CN=Optional Features,CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=contoso,DC=com’ –Scope ForestOrConfigurationSet –Target ‘contoso.com’
- You can do this from GUI also. Go to tools –> Active Directory Administrative Center, Right click on your domain and click on Enable Recycle Bin

- Activation VIA AD – Previously we used key management server to active all the client machines now it can be activated via AD which is much more integrated.
- Virtualizing DC – In earlier Server OS version there were some issue in VM DC Synchronization which has been improved in Windows 2012 Server.
- UI for Fine-Grained password policy – Now you can have separate password policy (In-term of length, complexity) within the same single domain and the UI to create policy is very cool.