I am using AWS for the last couple of months. The more I am exploring it, the more I am loving it. Thinking about doing a PhD on AWS (Just kidding).
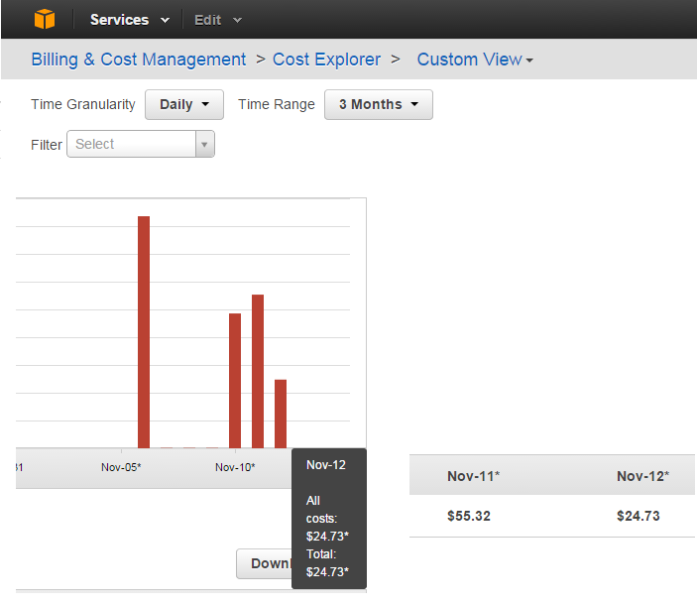
Since I am still using my credit card, sometimes it’s scary while running a large instance as pay per use model. What I have observed is most of my internal servers are only running during the office hour but they are generating cost as those are running instances. Below approach helps me to minimize 50% cost that was generating earlier.
Use AWS CLI
Using AWS CLI you can create a simple script which will run as a scheduler to stop and start any instance.
- Install AWS CLI (http://docs.aws.amazon.com/cli/latest/userguide/installing.html)
- Configure the tool as per the above link
- Create two batch files to start and stop your instances
In start batch file write the below command
aws ec2 start-instances –instance-ids [YOUR INSTANCE ID]
You will find the instance id in EC2 management console. Add multiple instance id in the same line with a space.
In stop batch file write the below command
aws ec2 stop-instances –instance-ids [YOUR INSTANCE ID]
You will find the instance id in EC2 management console. Add multiple instance id in the same line with a space.
- Create two windows scheduler and map those batch files to run as you want
I have seen a tremendous result in my environment after following this technique. I am still very new in AWS world and I am sure there may be several other techniques available to control the cost on AWS. Please do let me know if you are following any better approach.
Concern
- Do not store anything in the temporary drive AWS creates. AWS always refresh temporary drives data after restarting
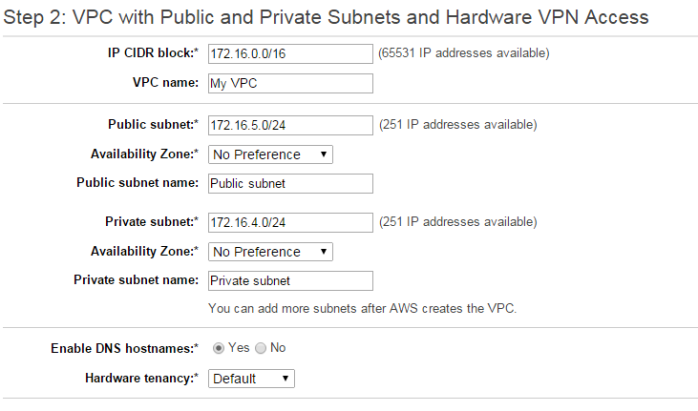
- Use VPC to have same private IP
- If you have public IP associated with an instance, use elastic IP as AWS will assign new public IP if you stop and restart an instance, in case you are not using any elastic IP